XSS attacks are a constant menace. They let bad guys put harmful code into web pages, which can lead to things like stealing important information, taking control of someone’s online session, and doing other bad things. In this context, the X-XSS-Protection header is a feature that helps keep websites and their users safe.
In this article, we will explore what is the X-XSS-Protection header, how it works, and why it’s really important to use it. We will also talk about its good and bad points and give advice on how to set it up properly.
Contents
What is the X-XSS-Protection header?
X-XSS-Protection is a security mechanism used in websites to prevent Cross-Site Scripting (XSS) attacks, which occur when malicious code, mostly JavaScript, is injected into web pages to hijack them or steal user data. Think of it as a security feature that detects and stops such attacks.
When you access a website, the web server may send an HTTP header called X-XSS-Protection in its response to your browser. This header tells your browser to activate its XSS defense. If your browser detects potentially harmful code on the page, it attempts to neutralize it before execution.
Mozilla’s article on this feature says that “The HTTP X-XSS-Protection response header is a feature of Internet Explorer, Chrome and Safari that stops pages from loading when they detect reflected cross-site scripting (XSS) attacks.”
The server-side configuration of this header can vary; it can instruct the browser to either block the suspicious code completely or simply notify the user about it.
To keep it simple, the header acts as a shield that protects your personal information and your browser’s integrity while browsing websites. It prevents attackers from injecting malicious code that could compromise your data.
BuiltWith usage statistics tell us that, among the top 1 million sites in the world, more than 125.000 use this header.
The meaning of X-XSS-Protection
This is an HTTP response header that stands for “Cross-Site Scripting Protection” and serves as a protective shield for websites. It instructs web browsers to defend against Cross-Site Scripting (XSS) attacks.
When a web server employs this feature, the browser activates its innate protective measures. If it identifies a XSS attack, it prevents the malicious code from causing harm, ensuring the safety of users. Web developers can use this feature to get the right balance between security and compatibility with older web components. This protective barrier stops harmful scripts and plays a crucial role in safeguarding user data.
Consequences of disabling the X-XSS-Protection
If this header is not configured on a website, it increases the vulnerability to XSS attacks. This HTTP header serves as a preventive measure against XSS attacks by activating the XSS filter within web browsers.
When it’s left unconfigured, browsers might fail to detect or block malicious code, thus allowing attackers to execute unauthorized scripts in users’ browsers. This can result in the compromise of sensitive data, session takeover, or harm to the website’s reputation. Enabling this feature is key for safeguarding user security and privacy.
Is X-XSS-Protection obsolete?
This header works by detecting potential XSS attacks in a web page’s JavaScript code and blocking them. However, there have been discussions about whether it is necessary to continue using it due to some issues:
- Possible decrease in security: in certain instances, it may be viewed as outdated because it takes a reactive stance rather than a proactive one. It obstructs potentially malicious JavaScript code but doesn’t address the root causes of XSS vulnerabilities.
- Limited browser support: most web browsers have either ceased to support X-XSS-Protection or have disabled this functionality by default due to concerns about potential security vulnerabilities. This has raised doubts about its practicality.
- Emphasis on enhanced security practices: instead of relying exclusively on it, more robust security methodologies are advocated, such as implementing Content Security Policy (CSP). CSP offers a more effective means of stopping XSS attacks by establishing rules about which resources can be loaded and executed on a webpage.
So, while this header is not considered completely obsolete, its utility has decreased due to its limitations and potential security issues. Currently, it is recommended to consider more robust features like CSP to protect websites against XSS attacks.
X-XSS-Protection browser compatibility
The header X-XSS-Protection is no longer considered an effective security measure in most modern web browsers. This is due to its outdated nature and the fact that it has been removed from most popular browsers because of potential security vulnerabilities.
Instead of using this header, it is advisable to employ Content Security Policy (CSP), which is a modern feature with broader support and provides enhanced protection against XSS attacks across all modern browsers.
This header used to work with certain browsers like Internet Explorer and older versions of Chrome, Edge, and Safari. It’s recommended to avoid relying on this header for your website’s security, unless there are special circumstances where you or your site’s users still utilize outdated web browsers.
The way hackers use XSS
Hackers employ XSS to sneak harmful code into websites or online apps. They do this by messing with input areas where users can type, like forms or comment boxes. When someone opens the page, the malicious code runs in their browser, stealing important stuff like passwords or session cookies. They might also redirect users to fake websites or infect their devices. Hackers can use XSS attacks to spread bad software, steal data, or even take over user accounts.
X-XSS-Protection header directives
The header offers several directives:
- “X-XSS-Protection: 0” turns off the XSS filter in the client’s browser.
- “X-XSS-Protection: 1” activates the XSS filter in the client’s browser but doesn’t notify the server of detected attacks.
- “X-XSS-Protection: 1; mode=block” enables the XSS filter in the client’s browser and blocks the webpage if an XSS attack is detected.
- “X-XSS-Protection: 1; report=<reporting-uri>” enables the XSS filter in the client’s browser and, if an XSS attack is detected, sends a report to the server specified in “<reporting-uri>.”
Please remember that, unless you really need to use it for specific reasons, it is strongly recommended to use more up-to-date security policies like CSP.
X-XSS-Protection header syntax
The syntax of the this header is pretty simple:
X-XSS-Protection "<directive>"
Simply replace <directive> with the desired directive that you wish to employ, as explained above.
X-XSS-Protection header examples
Let’s see a few examples of how to use this header:
Enable XSS protection: this header prompts the web browser to activate XSS protection in block mode. If a potential XSS attack is detected, the browser will block the page to shield the user.
X-XSS-Protection: 1; mode=block
Enable XSS protection with error reporting: besides blocking the XSS attack, the browser will also transmit a report to the specified website (in this case, “https://example.com/xssreport”) to allow site owners to take measures against future attacks.
X-XSS-Protection: 1; mode=block; report=https://example.com/xssreport
Disable XSS protection: this header disables XSS protection in the browser.
X-XSS-Protection: 0
How to configure the X-XSS-Protection header
Setting up the header is pretty easy, so let’s see how to do it in Apache and Nginx.
Setting up the X-XSS-Protection header in Apache
Open the Apache configuration file, typically found at /etc/apache2/apache2.conf or /etc/httpd/conf/httpd.conf, depending on your distro. You can use a text editor like “nano”:
nano /etc/httpd/conf/httpd.conf
Add this line in the http headers section:
Header always set X-XSS-Protection "1; mode=block"
Save the file and restart Apache:
systemctl restart httpd
You can also enable it in your .htaccess file, just add this code:
<IfModule mod_headers.c> Header always set X-XSS-Protection "1; mode=block" </IfModule>
Remember that you will need the Apache module “mod_headers” installed.
How to enable the X-XSS-Protection header in Nginx
Open your site’s Nginx conf file, usually located in /etc/nginx/sites-available/ or /etc/nginx/conf.d/, depending on your distro. You can use a text editor like “nano” to open the file, for example:
nano /etc/nginx/conf.d/mysite.conf
Add the following header line in your server block:
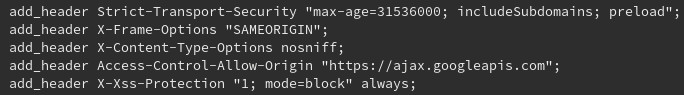
add_header X-XSS-Protection "1; mode=block";
You can also see it in the screenshot below along with other example security settings.
Save the file and test Nginx’s settings:
nginx -t
If the test is successful you can restart Nginx:
systemctl restart nginx
Testing the X-XSS-Protection configuration
If you want to test your current X-XSS-Protection settings, please follow this simple guide:
- Access our web security scanner.
- Type your domain in the scan box.
- Now tick the two boxes below, which are named ‘Clear cache’ and ‘Follow redirects’.
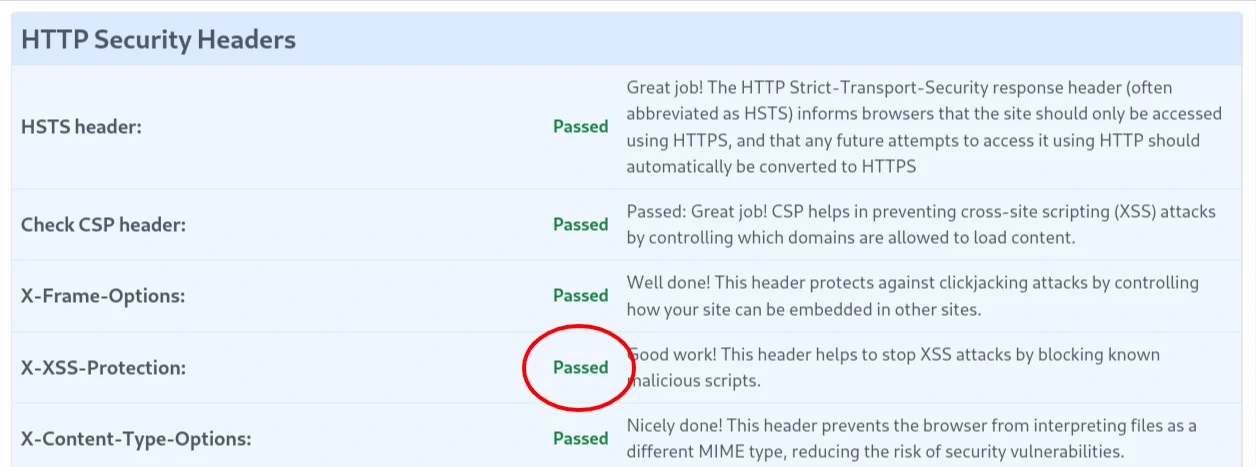
- Hit the Scan button.
- Now you have to scroll down to the section named ‘HTTP Security Headers’, and look for your ‘X-XSS-Protection’ test results: if you got a ‘Passed’ in green it means your header is set properly, however, getting a ‘Failed’ in red means that you will have to update your current settings.
X-XSS-Protection FAQ
What is X-XSS-Protection?
It is an HTTP header designed to prevent XSS attacks in websites. Its primary role is to identify and stop XSS attacks by inspecting JavaScript code within server responses, preventing the execution of malicious scripts in the user’s browser.
Is X-XSS-Protection a vulnerability?
No, it isn’t a vulnerability in itself. Instead, it functions as a security measure aimed at safeguarding against XSS vulnerabilities by obstructing unauthorized script execution in the user’s browser. However, its effectiveness can fluctuate based on the website’s settings and implementation.
Is X-XSS-Protection worse than CSP?
X-XSS-Protection and Content Security Policy (CSP) are different security measures. CSP is a powerful security feature that uses rules to control the loading and execution of resources on a web page, while the other focuses on identifying and preventing XSS attacks on the client side. Generally, it is advisable to employ CSP, because X-XSS-Protection is considered outdated and obsolete. So, in a few words, the answer is yes, X-XSS-Protection can be considered worse than CSP.
Summary
X-XSS-Protection is a security feature used to protect websites and their users against XSS attacks, which involve injecting malicious JavaScript code into web pages. When implemented, the X-XSS-Protection header instructs web browsers to activate an XSS filter that detects and stops the execution of malicious code.
While X-XSS-Protection has been effective in the past, nowadays it faces challenges, such as decreased browser support and a reactive approach to security. Due to this, other security features like CSP are recommended instead.